Global data privacy is no longer a regional concern but a global imperative, as data travels across borders at the speed of technology and touches every facet of modern business—from customer experiences and product design to partner ecosystems and regulatory risk, spanning industries from fintech to healthcare. To thrive in this environment, organizations must design and implement robust governance for cross-border data transfer, align operations with data privacy laws that vary by market, and bake privacy by design into products, processes, and supplier relationships to reduce risk and accelerate innovation, while building trust with customers who expect responsible data stewardship. A mature global privacy program goes beyond compliance, supporting innovation while meeting GDPR requirements and ensuring CCPA compliance expectations in the United States, all within a scalable framework that aligns executive priorities with privacy controls, incident response readiness, and transparent data handling across jurisdictions, with governance that translates into measurable performance indicators. This introductory guide outlines a practical framework for data mapping, risk assessment, and ongoing monitoring that translates complex regulatory nuance into repeatable controls, clear ownership, and measurable privacy outcomes across diverse markets, enabling teams to operate with confidence even as laws evolve, including data lineage, DPIAs, and risk scoring to prioritize remediation. By embedding privacy as a strategic capability—anchored in transparency, accountability, and continuous improvement—organizations can safeguard data, earn trust, and sustain competitive advantage as global data flows accelerate, while maintaining a defensible posture against evolving enforcement paradigms.
Beyond the page title, the topic can be framed through related concepts such as the international data protection landscape, cross-border information governance, and personal data safeguards that span multiple regulatory regimes. In practical terms, this means data flow mapping, data sensitivity classification, encryption and access controls, and sustained collaboration among legal, security, product, and procurement teams to align risk tolerance with business objectives and customer expectations. From a broader perspective, the discussion touches on governance models, regulatory regimes, data subject rights, and transparency initiatives that enable organizations to scale their privacy program across borders while remaining adaptable to new requirements.
Global Data Privacy in Practice: Navigating Cross-Border Data Transfer and GDPR-Driven Compliance
Global data privacy is no longer a regional concern; it has become a universal imperative as data flows across borders at the speed of technology. A practical program aligns cross-border data transfer with evolving data privacy laws while preserving innovation, trust, and user rights. The GDPR remains the dominant benchmark, influencing how organizations structure processing, consent, data subject rights, and breach notification even when data moves outside the EU.
To translate this into action, establish governance, data mapping, and a risk-based approach to transfers. Apply privacy by design and DPIAs for high-risk activities, implement standard contractual clauses (SCCs) where needed, and supplement with encryption and least-privilege access. This foundation supports a scalable global program that adapts to new laws without slowing growth and builds trust with customers and regulators alike.
GDPR and CCPA Across Borders: Building Privacy by Design for Cross-Border Data Transfer
Across borders, GDPR-inspired data privacy laws and CCPA compliance expectations shape how data moves and how cross-border data transfer is managed, including how consent is obtained and how rights are exercised. A resilient program begins with data mapping, a lawful basis assessment under GDPR, and alignment with CCPA requirements for transparency and data minimization. Treat privacy by design as a core engineering principle that embeds privacy controls into products and partnerships from day one.
Practical next steps include establishing data transfer mechanisms (SCCs or adequacy-equivalent options), conducting DPIAs for high-risk processing, and enforcing robust vendor management. Implement end-to-end security controls, monitor regulatory developments across jurisdictions, and train teams to handle data subject requests efficiently. This approach delivers compliant cross-border data transfer while sustaining innovation and customer trust.
Frequently Asked Questions
What is Global data privacy and how do cross-border data transfer and GDPR shape compliance?
Global data privacy refers to universal principles for collecting, using, and transferring personal data across borders. For cross-border data transfer, organizations rely on mechanisms such as Standard Contractual Clauses (SCCs) and adequacy decisions, while applying privacy by design and DPIAs to manage risk and protect individuals’ rights. GDPR remains the benchmark guiding data privacy laws worldwide, shaping governance, transparency, and breach notification expectations even when data does not originate in the EU. A practical program maps data flows, establishes lawful bases, and enforces governance to build trust and minimize regulatory risk.
What practical steps can organizations take to implement a scalable Global data privacy program addressing cross-border data transfer and privacy by design?
Start with data inventory and mapping to identify data flows and processing purposes. Establish governance with a privacy lead and clear responsibilities for data subject rights, incident response, and vendor management. Define lawful bases and purpose limitations aligned with GDPR, while applying data minimization. Implement transfer mechanisms (SCCs or adequacy) and add technical measures like encryption, pseudonymization, and strict access controls. Apply privacy by design and DPIAs for high-risk processing, and maintain ongoing vendor management, incident response readiness, and a process for data subject rights requests. Monitor evolving data privacy laws (including GDPR and CCPA compliance) and adapt controls across regions as regulations evolve.
| Topic | Key Points |
|---|---|
| Global Data Privacy Imperative | Data crosses borders rapidly; the modern digital economy relies on cross-border collaboration, cloud services, and real-time analytics. Regulators worldwide are tightening guardrails, making a global privacy program essential to build trust and manage risk. |
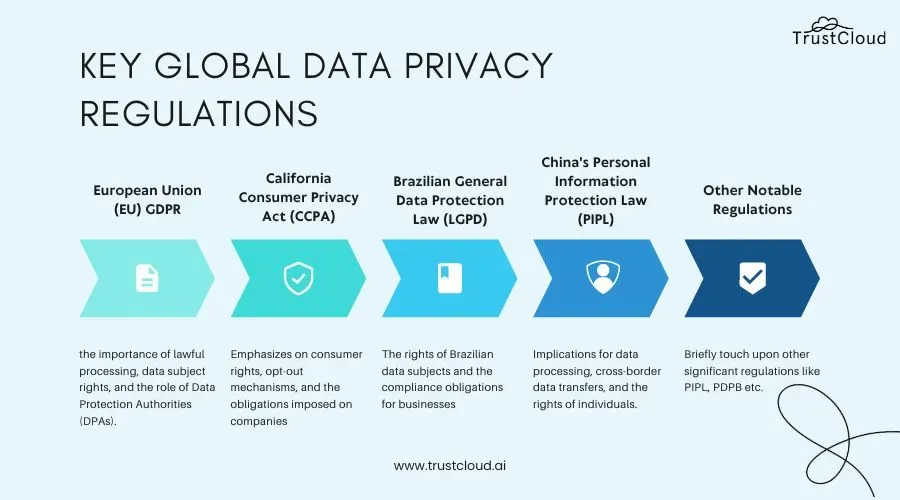
| Regulatory Landscape | GDPR remains a universal benchmark; GDPR-inspired regimes shape handling of personal data across borders. Other major regimes include CCPA/CPRA (US), LGPD (Brazil), PIPL (China), PDPA (Thailand), APPI (Japan), and evolving Indian rules. Principles emphasize fairness, transparency, and purpose limitation. |
| Core Privacy Principles | Anchor strategy in lawful bases, data minimization, purpose limitation, accuracy, and accountability. Apply universal privacy principles while accommodating jurisdiction-specific requirements. |
| Cross-Border Data Transfers | Key mechanisms include SCCs, adequacy decisions, and other recognized bases. Implement supplementary measures (encryption, pseudonymization, least privilege) and DPIAs for complex transfers; ensure clear roles for controllers/processors and robust documentation. |
| Practical Challenges | Data localization pressures, government access demands, and balancing national security with individual privacy. Address with end-to-end encryption where feasible and strong breach notification and incident response capabilities. |
| Global Program Framework | Build a repeatable process: data inventory/mapping, governance roles (DPO/privacy lead), lawful bases mapping, transfer mechanism selection, DPIAs, vendor management, data subject rights programs, security controls, incident response, regulatory monitoring, and governance cadence. |
| Common Pitfalls | Over-reliance on a single transfer mechanism, incomplete data mapping, weak localization strategy, delayed rights responses, and lack of transparency. Regular risk reviews and clear customer communication help sustain trust. |
| Real-World Scenarios | Multinational data processing across EU, North America, and APAC requires data inventory, transfer mapping, SCCs where needed, DPAs with processors, DPIAs for high-risk activities, encryption, access controls, and ongoing staff training. |
| Path Forward | Build resilience through governance, technology, and culture. Privacy by design, ongoing playbooks, and cross-border collaboration enable faster growth while protecting rights and sustaining competitive advantage. |
Summary
Table summarizing the key points of Global Data Privacy content: imperative of global scope, regulatory landscape, core principles, cross-border transfers, practical challenges, program framework, common pitfalls, real-world scenarios, and the path forward.