Global cybersecurity essentials are redefining how organizations protect critical assets in today’s interconnected digital landscape. By aligning with cybersecurity best practices for organizations, firms can reduce risk while boosting stakeholder confidence. These efforts align with enterprise cybersecurity strategies that scale across departments and geographies, and they address security essentials for modern businesses facing multi-cloud and supply chain challenges. A practical, proactive posture emphasizes cyber threat prevention and response, enabling rapid detection, containment, and recovery when incidents occur. Adopting a global cybersecurity framework helps standardize controls, metrics, and governance while remaining adaptable to evolving threats.
Viewed through an alternative lens, the same idea translates into global cyber risk management and security fundamentals that organizations use to safeguard data and operations. In practice, this means building a strong security posture, rigorous cyber hygiene, and resilient defenses that span people, processes, and technology. Threat detection, incident response, and continuity planning are framed as governance and risk controls, integrated with privacy-by-design and data minimization. Ultimately, the goal is a scalable, repeatable program that protects information assets across on-premises, cloud, and partner ecosystems.
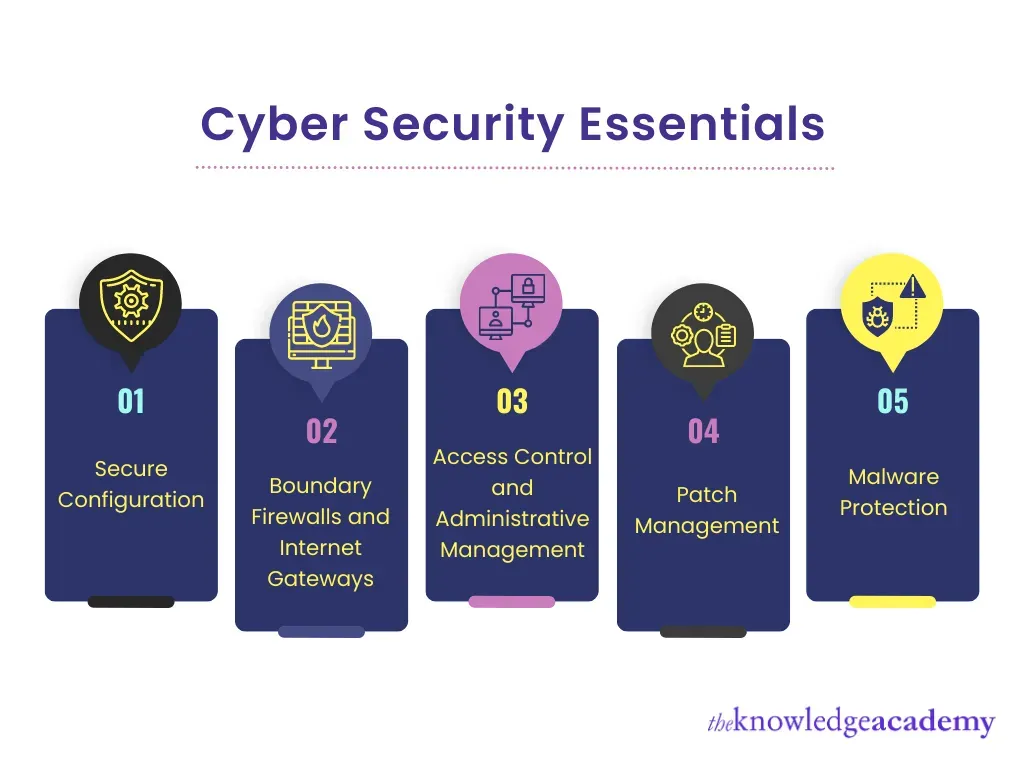
Global cybersecurity essentials: A foundation for security in modern businesses
Global cybersecurity essentials are foundational as organizations navigate cloud adoption, remote work, and extended supply chains. A robust program depends on a layered defense and alignment with business objectives, delivering resilience, trust, and continuity. The core pillars—Identity and Access Management (IAM) with Zero Trust principles; Endpoint Security and device hygiene; Network segmentation and perimeter controls; Secure Software Development Lifecycle (SDLC) and supply chain security; Data protection and encryption; Cloud security and multicloud governance; Cloud-native security, observability, and threat detection; Incident response and resilience; and Security operations, metrics, and governance—work in concert to reduce risk, improve visibility, and accelerate detection and response. These pillars are not one-off tasks but ongoing capabilities that connect people, process, and technology to protect critical assets. When aligned with a global cybersecurity framework, they provide consistent controls across regions and vendors, enabling cyber threat prevention and response.
Implementing these essentials begins with governance, risk assessment, and a phased approach. Start with foundational controls—identity governance, asset inventory, basic monitoring—and then expand to secure SDLC, data protection, and cloud security. Adopting mature security operations, metrics dashboards, and governance ensures ongoing improvement and alignment with cybersecurity best practices for organizations. These efforts translate into security essentials for modern businesses, aligning with broader enterprise cybersecurity strategies that scale across departments and geographies, while meeting regulatory expectations and customer commitments.
Scalable enterprise cybersecurity strategies: governance, risk, and resilience
Scalable enterprise cybersecurity strategies demand a risk-based mindset. Begin with a formal asset inventory, data classification, and business impact analyses to focus protections where they matter most. Privacy-by-design and data minimization reduce exposure, while practical controls like MFA for remote access and consolidated identity stores limit identity sprawl. These steps embody enterprise cybersecurity strategies that scale, enabling consistent enforcement of least-privilege access and rapid containment of incidents. By prioritizing risk scenarios and aligning resources to the most significant threats, organizations can build a defense that grows with their operations and regulatory requirements.
Beyond technology, governance, training, and culture complete the cycle. Align controls with a global cybersecurity framework and applicable regulations, conduct regular risk assessments and penetration testing, and publish clear metrics that demonstrate value to leadership. Build security-aware teams through phishing simulations, secure coding workshops, and tabletop exercises, while maintaining mature security operations with SIEM, UEBA, and automated response. This holistic approach ensures cyber threat prevention and response, resilience, and ongoing improvement across the security program, reinforcing cybersecurity best practices for organizations and supporting secure, scalable enterprise operations.
Frequently Asked Questions
What are the core pillars of global cybersecurity essentials that organizations should implement as security essentials for modern businesses?
Global cybersecurity essentials rest on a set of core pillars that reduce risk, improve visibility, and enable rapid response. Key pillars include Identity and Access Management (IAM) and Zero Trust; Endpoint security and device hygiene; Network segmentation and perimeter controls; Secure Software Development Lifecycle (SDLC) and supply chain security; Data protection, privacy, and encryption; Cloud security and multicloud management; Cloud-native security, observability, and threat detection; Incident response, recovery, and resilience; and Security operations, governance, and metrics. Implement these in phased plans (foundational controls, expanded coverage, and resilience) and align governance to a global cybersecurity framework. This approach supports cyber threat prevention and response while strengthening security for modern businesses.
How can organizations align with a global cybersecurity framework and enterprise cybersecurity strategies to improve cyber threat prevention and response?
To scale with a global cybersecurity framework and enterprise cybersecurity strategies, start with risk-based asset inventory, data classification, privacy-by-design, and multi-factor authentication. Consolidate identity stores to reduce identity sprawl, enforce least-privilege access, and protect data at rest and in transit. Strengthen the supply chain with SBOMs and vendor risk management. Integrate security into the SDLC and extend controls to cloud and multicloud environments. Deploy continuous monitoring, SIEM/UEBA, and automated response to detect and respond to incidents quickly. Develop incident response playbooks and runbooks, and train teams through phishing simulations and secure coding workshops. Measure progress with KPIs (MTTD, MTTR, patch adoption, MFA coverage) and conduct regular audits and independent testing to verify alignment with the global cybersecurity framework and strengthen enterprise cybersecurity strategies against evolving threats.
| Pillar | Key Points |
|---|---|
| Identity and Access Management (IAM) and Zero Trust | Strong authentication; least-privilege access; continuous verification; federated identities; step-up risk-based access decisions to reduce credential abuse. |
| Endpoint Security and Device Hygiene | Layered protection for modern devices: anti-malware, EDR, encryption, regular patching; unified endpoint management to maintain consistency. |
| Network Segmentation and Perimeter Controls | Limit breach blast radius and deter lateral movement with firewalls, intrusion prevention, and micro-segmentation. |
| Secure SDLC and Supply Chain Security | Security integrated into development and vendor management: code reviews, automated testing, dependency management, SBOMs. |
| Data Protection, Privacy, and Encryption | Data classification, DLP, encryption at rest/in transit, and clear data handling policies across on-premises, cloud, and hybrid environments. |
| Cloud Security and Multicloud Management | Centralized governance, consistent security controls, and cloud-native protections across multiple cloud platforms. |
| Cloud-native Security, Observability, and Threat Detection | Continuous monitoring, log aggregation, anomaly detection, and timely insights to accelerate detection and response. |
| Incident Response, Recovery, and Resilience | Preparedness with playbooks, runbooks, tabletop exercises; rapid detection, containment, eradication, and recovery. |
| Security Operations, Metrics, and Governance | SIEM/UEBA, threat intelligence, automated responses; dashboards, risk heat maps, and governance to demonstrate value. |
Summary
Concise HTML table has been prepared to explain the key points of Global cybersecurity essentials in English. The table highlights the core pillars and their practical focus areas, illustrating how organizations can implement a layered, risk-based security program. A concluding paragraph follows to describe the topic in a descriptive style and emphasizes ongoing improvement, governance, and measurement to sustain resilient cybersecurity postures.