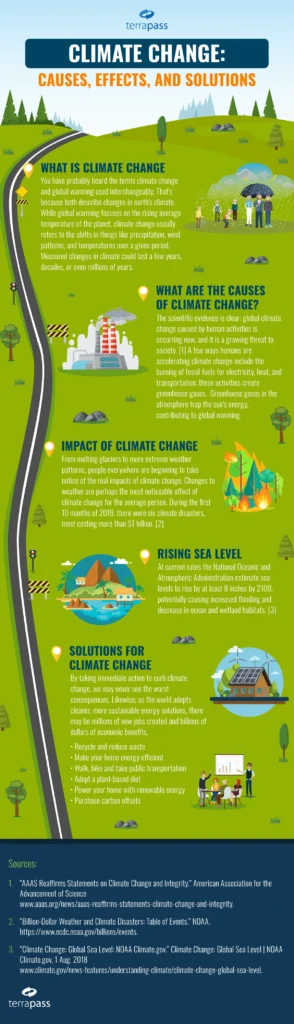
Global Data Privacy has moved beyond borders to become a defining framework for organizations worldwide, shaping product development, risk planning, and stakeholder trust across markets. As data flows accelerate in today’s digital economy, individuals seek clear controls over their information, and regulators respond with evolving rules that tighten obligations while encouraging innovation. A robust approach aligns data privacy regulations with practical privacy by design, helping teams ship secure products while safeguarding user trust and enabling compliant analytics. Strong governance, clear policies, and continuous education ensure programs stay resilient as new requirements emerge, helping teams maintain alignment with evolving expectations. This alignment also supports responsible data handling across borders, reinforces security, and demonstrates a long-term commitment to governance, accountability, and global trust.
From a broader angle, the privacy conversation is framed by international data protection regimes that span multiple jurisdictions and aim to harmonize expectations. Think of it as a global posture of information governance where data handling laws, consent models, and risk assessments intersect with industry standards and consumer rights. In practice, organizations map data flows, evaluate risk, and implement transparent practices that align with both local requirements and the broader trend toward interoperable privacy principles.
Global Data Privacy: Navigating a Multinational Regulatory Landscape
Global Data Privacy marks a shift from local compliance to a cross-border framework that governs how personal data moves across continents. As data flows accelerate in today’s digital economy, individuals expect clear controls over their information, and regulators respond with rules that prioritize transparency, consent, and accountability. Organizations must understand how data privacy regulations interact with global privacy laws, because data often travels across borders between customers, employees, suppliers, and service providers. This reality makes data governance a strategic capability, not a mere checkbox on a compliance checklist.
To operate effectively, leaders should map data assets and flows, assess cross-border data transfers, and stay current with changes to data privacy regulations and global privacy laws. A mature approach combines risk-based data minimization with privacy by design principles, ensuring privacy is embedded into product development, data architectures, and vendor relationships. By articulating DPIAs, retention policies, and consent management, organizations can demonstrate accountability while maintaining agility in data-driven innovation. It also helps with regulatory reporting and building trust with customers and partners.
Best Practices for Implementing a Global Privacy Program: From Privacy by Design to Consent Management
Best practices for a global privacy program start with governance that aligns leadership, policy, and risk appetite, then translate into people, processes, and technology. Embedding privacy by design across product lifecycles reduces regulatory friction and supports scalable compliance with data privacy regulations and global privacy laws. A centralized program should also address consent management, ensuring that notices are clear, revocable, and auditable as data moves through cross-border data transfers.
Practical steps include standardizing privacy templates and data mappings, DPIA templates, and incident response playbooks, along with robust security controls such as encryption and access management. For cross-border data transfers, monitor transfer mechanisms and vendor risk, maintain auditable records, and ensure ongoing governance. Training staff to recognize privacy risks and to respond to data subject rights requests promptly helps close the loop between policy and operation.
Frequently Asked Questions
What is Global Data Privacy and why are cross-border data transfers a regulatory focus?
Global Data Privacy refers to a worldwide approach to protecting personal data as it moves across borders. Regulators worldwide enforce data privacy regulations and global privacy laws, making cross-border data transfers a key compliance focus. To stay compliant, organizations should map data flows, implement lawful transfer mechanisms (such as SCCs), conduct DPIAs, monitor vendors, and maintain breach readiness.
How can privacy by design and consent management help organizations comply with global privacy laws and data privacy regulations?
Privacy by design embeds privacy into products and processes from the start, aligning with global privacy laws and data privacy regulations. Consent management provides clear, granular, and revocable consent, supports records of processing, and helps fulfill data subject rights requests. Together, they enable transparency, reduce risk, and facilitate DPIAs, data minimization, and secure data flows across borders.
| Key Topic | Summary |
|---|---|
| Global Data Privacy defined | A core principle is that personal data should be processed lawfully, fairly, and transparently; governance spans borders and treats cross-border data flows as a strategic capability. |
| Global landscape | Regulations differ by regime (EU GDPR, US sectoral laws, and emerging comprehensive laws); organizations operate across borders, requiring harmonized privacy expectations while enabling innovation. |
| What’s New: Navigating New Rules | Regulators tighten data transfer mechanisms, consent, DPIAs, breach notifications, and individuals’ rights; SCCs are evolving; there is increased focus on accountability and cross-border processing. |
| Best Practices for a Global Privacy Program | Start with strategy and governance, then scale through people, processes, and technology: map data assets, classify data, embed privacy by design, manage consent, safeguard cross-border transfers, manage vendors, establish governance with KPIs, invest in security, plan for breaches, and foster privacy awareness. |
| Practical Steps for Global Operations | Standardize privacy templates and processes; centralize governance with local adaptations; bake data minimization into roadmaps; define retention/deletion policies; maintain auditable records; layered security; align incident response with regulations. |
| Technology, Security, and the Future of Global Data Privacy | Encryption and access controls are essential; consider PETs, zero-trust models, and ongoing risk assessments; anticipate regulatory convergence, AI/privacy governance, and adaptable privacy programs. |
| Common Challenges and How to Overcome Them | Fragmented data landscapes, slow responses to rights requests, vendor risk management overload, and balancing privacy with innovation; tackle with data mapping, automated workflows, standardized vendor due diligence, and privacy-by-design as a competitive advantage. |
Summary
table